Why Distributed Systems Fail? (part 2)

In the first part of our exploration into the fallacies of distributed computing, we looked into four common misconceptions that can significantly impact the design and functionality of distributed systems: the reliability of the network, the illusion of zero latency, the myth of infinite bandwidth, and the false sense of inherent network security.
Now, in Part 2 of this series, we turn our attention to the remaining four fallacies, each presenting unique challenges and requiring careful consideration:
Topology Doesn't Change: The oversight of network dynamics and their impact on system performance.
There is One Administrator: The simplification of management responsibilities and control in distributed environments.
Transport Cost is Zero: The underestimation of the resources required for data movement across the network.
The Network is Homogeneous: The assumption that the network environment is uniform and consistent.
Fallacy 5: Topology Doesn't Change
This one is a misconception in distributed computing that disregards the dynamic nature of network topologies. Network topology, the arrangement of various elements (links, nodes, etc.) in a computer network, is not static. Changes can occur due to network expansion, hardware upgrades, outages, or reconfigurations. Designing systems under the assumption of a static topology can lead to significant issues when inevitable changes occur.
System Rigidity: Systems designed for a fixed topology may lack the flexibility to adapt to changes, leading to failures or suboptimal performance.
Maintenance Challenges: Regular updates or modifications can become cumbersome and risky in a rigidly designed system.
Scalability Issues: A system that doesn't account for changing topology might struggle to scale efficiently as the network grows or evolves.
Inefficient Resource Utilization: Fixed-topology assumptions can lead to poor resource allocation, as the system cannot dynamically adjust to the most efficient paths or nodes.
Mitigation Strategies:
Dynamic Configuration: Implement mechanisms that allow the system to automatically adapt to changes in network topology.
Regular Monitoring and Updates: Continuously monitor network topology and perform regular updates to ensure the system aligns with the current network state.
Decentralization: Avoid single points of failure by decentralizing functions and resources where feasible.
Redundancy: Incorporate redundancy in network paths and nodes to maintain functionality even if parts of the network change or fail.
Flexible Protocols: Use network protocols that can handle changes in topology without significant disruption.
Testing for Variability: Regularly test the system under varying topological conditions to ensure robustness against changes.
Documentation and Communication: Maintain clear documentation of the network topology and ensure effective communication among team members about changes.
By acknowledging and preparing for the inevitability of changing network topologies, distributed systems can be made more adaptable, resilient, and efficient.
Fallacy 6: There is One Administrator
The belief that 'There is One Administrator' is a fallacy in distributed computing that oversimplifies the management and control of distributed systems. In reality, distributed systems often span multiple administrative domains, each with its own policies, procedures, and management styles. Assuming a single administrative control point can lead to serious misjudgments in system design, particularly in areas related to governance, security, and resource sharing.
Implications:
Coordination Challenges: Multiple administrators mean coordination becomes more complex, and unilateral decisions are often impractical.
Security Policy Conflicts: Differing security policies and practices across administrative domains can lead to inconsistencies and vulnerabilities.
Resource Management Issues: Assumptions about resource control and allocation can be misguided when multiple administrators are involved.
Compliance Complications: Adhering to various regulatory and policy requirements can be challenging in a multi-administrator environment.
Mitigation Strategies:
Distributed Governance: Establish a governance model that accommodates input and decision-making from all administrative domains.
Unified Security Standards: Work towards a common set of security standards and practices that are agreeable and applicable across all administrative areas.
Flexible Resource Allocation: Implement resource management systems that are flexible and can adapt to the needs and policies of different administrators.
Clear Communication Channels: Ensure clear and effective communication channels among various administrators to facilitate coordination and conflict resolution.
Decentralized Control Mechanisms: Use decentralized control mechanisms where possible to allow for autonomy within different administrative domains.
Comprehensive Documentation: Maintain detailed documentation of system policies, procedures, and agreements that involve multiple administrative domains.
Recognizing the reality of multiple administrators in distributed systems and adopting these strategies can greatly enhance the management, security, and overall functionality of these complex environments.
Fallacy 7: Transport Cost is Zero
A common fallacy in distributed computing, which overlooks the resources required for data movement across a network. This fallacy ignores the costs associated with bandwidth usage, latency, and the energy required for data transmission. In reality, transporting data, especially large volumes over long distances, incurs significant costs and can impact system performance and efficiency.
Implications:
Resource Inefficiency: Ignoring transport costs can lead to inefficient use of network resources, such as bandwidth and energy.
Increased Operational Costs: Overlooking the cost of data movement can result in unexpectedly high operational expenses, especially in cloud-based services where data transfer fees are involved.
Performance Bottlenecks: Underestimating transport costs can cause bottlenecks in system performance, particularly when large data transfers are frequent.
Mitigation Strategies:
Data Localization: Keep data as close as possible to its primary users to minimize unnecessary data movement.
Bandwidth Management: Monitor and manage bandwidth usage to optimize data transfer processes and reduce costs.
Data Compression: Employ data compression techniques to reduce the size of data being transported.
Cost-Aware Architecture Design: Design system architectures with a focus on minimizing and optimizing data transport.
Selective Data Movement: Be selective about what data needs to be moved and when, avoiding unnecessary data transfers.
By acknowledging the real costs associated with data transport in distributed systems and implementing these mitigation strategies, it is possible to build more efficient, cost-effective, and environmentally friendly systems.
Fallacy 8: The Network is Homogeneous
The assumption that 'The Network is Homogeneous' is a fallacy in distributed computing that ignores the diversity in network environments. This fallacy leads to the expectation that all parts of a network will behave similarly and support the same protocols, performance levels, and features. In reality, networks are composed of a variety of devices, technologies, and configurations, each with its own characteristics and limitations.
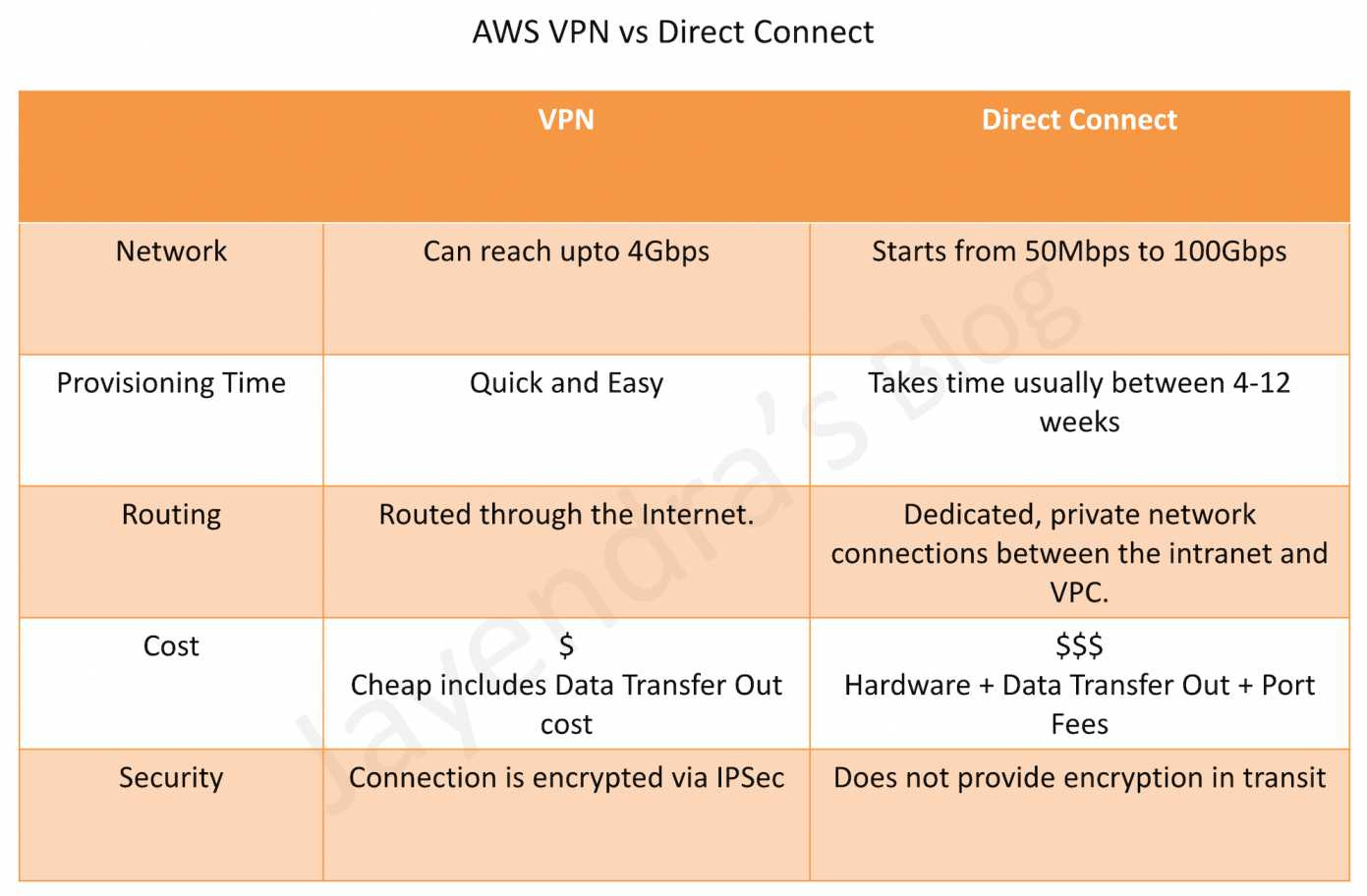
For instance, this image above taken from this post shows the various differences in performance, cost, time, and security between AWS VPN and Direct Connect.
Implications:
Compatibility Issues: A homogeneous network assumption can lead to compatibility problems when systems encounter different network technologies.
Performance Variability: Disregarding network diversity can result in unpredictable performance, as different network segments may have varying capacities and speeds.
Scalability Challenges: Scaling a system becomes more complex when it needs to adapt to diverse network environments.
Inadequate Error Handling: Systems might not be equipped to handle the range of errors that can occur in a heterogeneous network.
Mitigation Strategies:
Cross-Network Compatibility: Design systems and protocols to be compatible with a range of network technologies and standards.
Adaptive Performance Tuning: Implement mechanisms that dynamically adjust performance based on the current network environment.
Extensive Testing: Test systems in a variety of network conditions to ensure robustness and adaptability.
Flexible Architecture: Build a flexible and modular architecture that can easily adapt to different network settings.
Detailed Network Analysis: Regularly analyze the network to understand its composition and tailor the system accordingly.
Robust Error Handling: Develop comprehensive error handling that can manage the diverse failures and issues that arise in heterogeneous networks.
User-Aware Optimization: Optimize system performance based on the specific network characteristics of different user segments.
Continuous Monitoring and Updates: Continuously monitor network performance and update the system to handle evolving network environments.
Recognizing the diversity in network environments and adopting these strategies helps in building distributed systems that are more resilient, adaptable, and capable of operating efficiently across heterogeneous networks.